Secure and reliable Wireless Networking
The IoT Revolution for commercial Buildings
Fortsetzung des Artikels von Teil 2
Routing by HOP List
The NWK header (Figure 8) defines the »Hop List«, a given route through the network (Figure 9). The message from the application is organized in the packet and routed through the network according to the hop list — in dual band and via the switching nodes of the meshed network. The hop list delivers the next hop thanks to the asynchronous meshed network with minimal computing effort – an important skill that ensures low latency and low energy consumption of the individual network nodes (sensors).
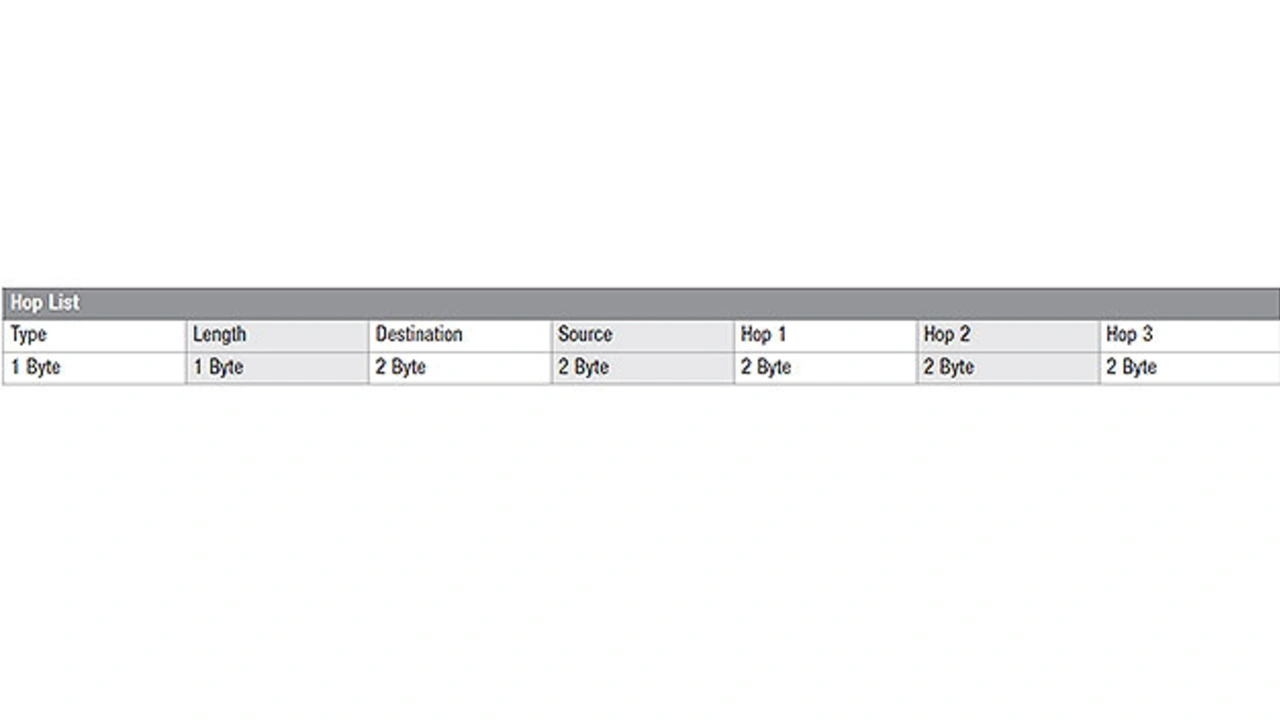
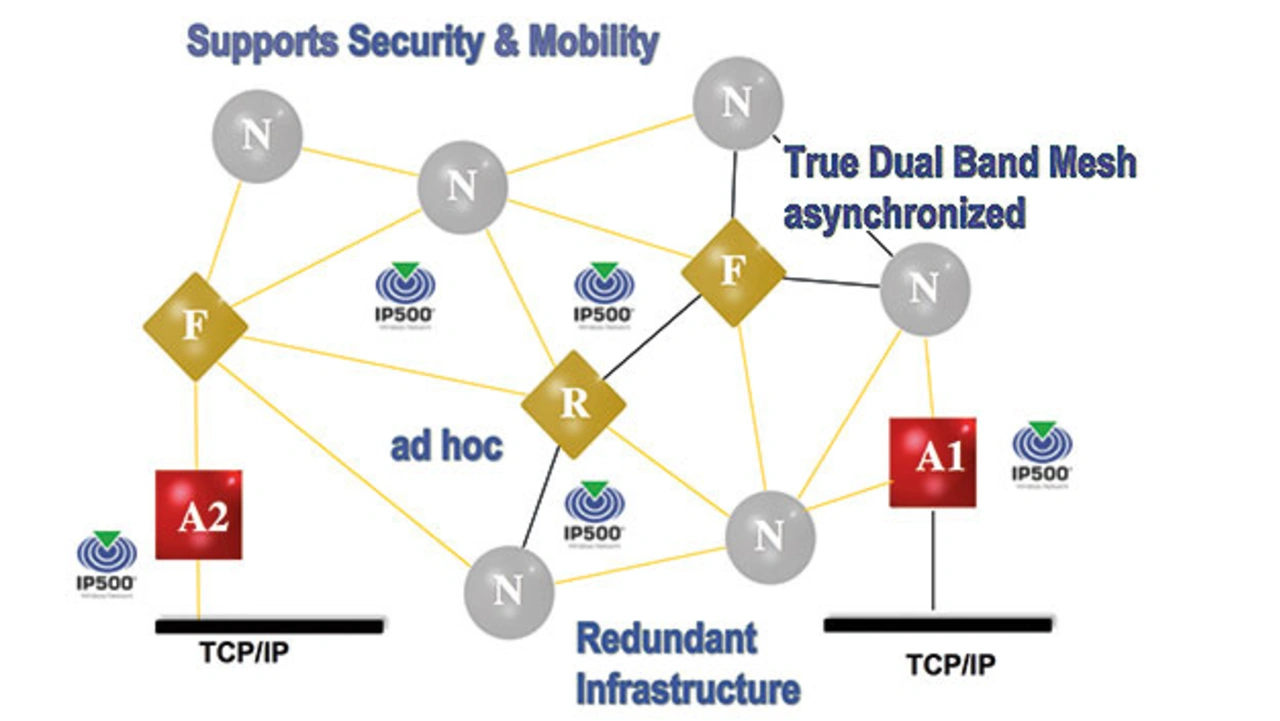
The node sending a message determines the hop list for the data packet from its routing table by forming the shortest route. This process offers the end user a self-healing, self-configuring mesh network with the lowest latency.
All messages of the IP500 application layer are sent in both directions between the nodes and the gateway, which is why each node and the gateway knows the route without any computing effort. Additionally the most recently received messages are also stored in the gateway.
The use of alternative routes in the meshed network, together with the redundancy at the frequency level, ensures high reliability and low latency when interference occurs, which has been confirmed by VdS as the basis for pre-conformity with the European standards [2].
Security and Encryption in the IP500 Network
The calculation of the AES128 key for symmetrical encryption and decryption of the message is based on the sequence number of the message and a master key, which is carried out by an asymmetric ECDH method (Elliptic-curve Diffie-Hellman) between each individual node and the Gateway. End-to-end encryption ensures that the messages cannot be intercepted or forged by forwarding nodes. Using the AES128 key once for a single message increases the security of the IP500 network.
Literature
[1] IP500 Alliance, www.IP500alliance.org
[2] DIN EN 50131-5-3: 2017-09; VDE 0830-2-5-3: 2017-09: Alarm systems – Intrusion and hold-up systems – Part 5-3: Requirements for transmission devices, wireless frequency technologies use; German version EN 50131-5-3: 2017.
The Authors

Helmut Adamski
is an IoT pioneer and currently leads the IP500 Alliance e.V. as CEO and chairman. He has more than 25 years of experience in the high-tech industry, with a focus on IoT and IT network applications, radio ICs and security applications for buildings and premises.
Adamski holds an engineering degree in electronics and attended Executive/MBA programs at the Institute of Excellence, San Diego, and Stanford University, California, USA.
helmut.adamski@ip500alliance.org

Witali Gisbrecht
is a specialist in the development of embedded software for network stacks, security methods and gateway architectures. He graduated from the University of Paderborn in 2007 with a Bachelor of Science degree in Computer Science.
- The IoT Revolution for commercial Buildings
- PRE-Compliance with European Standards
- Routing by HOP List
- IP500 Alliance








