Protection against hacking
Security first
Fortsetzung des Artikels von Teil 1
Preventing manipulation
Protection against manipulation involves defense mechanisms to prevent intentionally or unintentionally launched physical attacks on the hardware system outside the microcontroller. The backup domain, linked to various wake-up sources, ensures that protection is also maintained in low-power mode. The realtime clock (RTC) assigns a time stamp to each manipulation event.
Some STM32 series also have an RTC register protection function. It blocks illicit writing and works independently of system reset. But this does not include protection when typing a key sequence. Once manipulation is detected, the protection register ensures that the content written in the course of it is automatically deleted. Additionally, specific communication channels can be closed by a configuration lock that blocks selected general-purpose inputs/outputs (GPIOs). The lock can be canceled on the next reset.
Other weapons defending against attack
The debug lock prevents unauthorized access to the microcontroller via a debug interface. The security level is selectable depending on application and requirements, though it cannot be scaled back afterwards.
Access rights authorize users or groups of users to carry out specific actions. To that end, the integrated memory protection unit (MPU) divides memory into regions with differing rights and access rules. When data transfer is carried out, the firewall protects the code or data part of the flash memory, or SRAM, against code (fragments) running outside the protected sector. The firewall is more restrictive than the MPU; it is only integrated in the STM32L0 and L4. A read protection function is used to manage memory access control. It might be that this prevents memory dumps, such as backups of user IPs. Write protection protects each sector against unwanted write operations. Proprietary code protection allows each memory sector to be configured as “execute only”, meaning that code can only be run in it and not written. The mass erase and secure erase functions enable IPs and confidential data to be deleted safely; the action resets memory completely to its factory defaults.
To ensure traceability of an end-product many STM32 series feature a 96-bit unique ID. This can also be used to diversify security keys. Many series additionally incorporate secure firmware update functions. Hardware security functions can be expanded further by software-based measures.
Security of an end-product against manipulation by third parties is based on the software solutions implemented and electronic hardware components used. Microcontrollers and memory chips – where appropriate in combination with sensors and application-specific ICs – are key to IoT applications and industry 4.0 alike. In its white paper [1] Rutronik has compiled a set of integrated security features for microcontroller families: it includes tables listing systems for protection against manipulation, encryption modules, permission management, debug lock level, memory protection, as well as integrity and functional security.
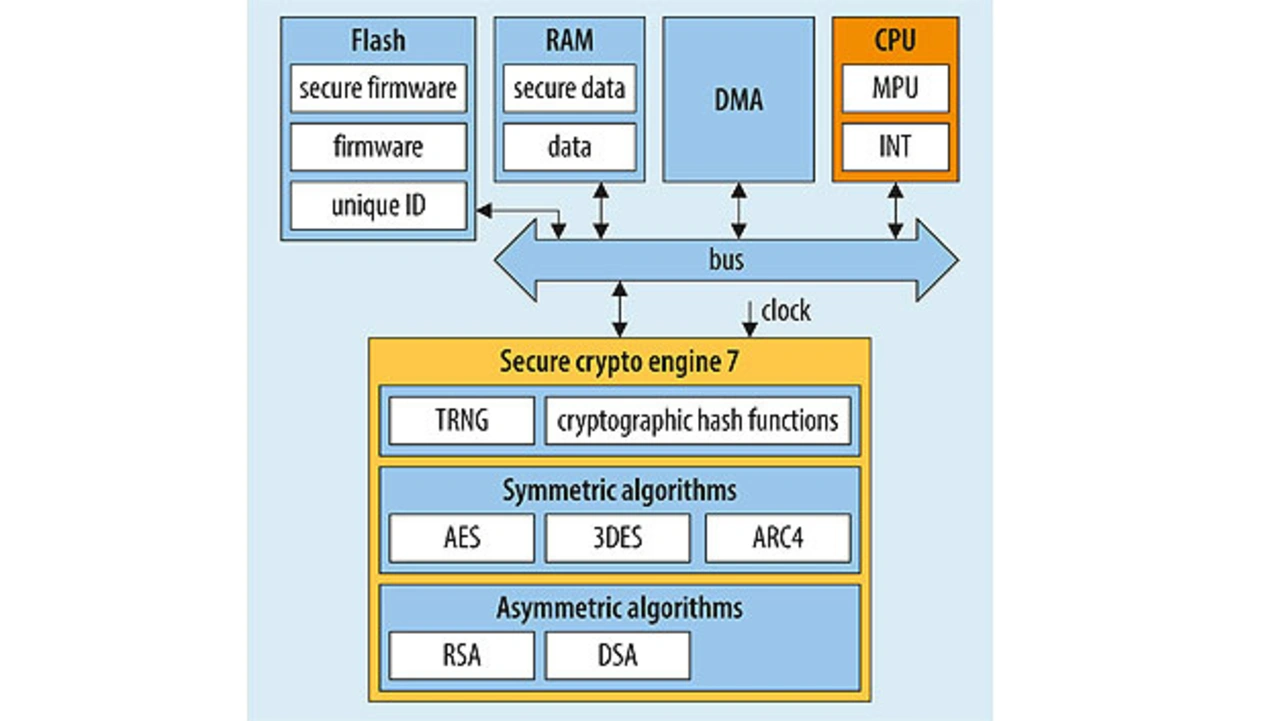
Like various STM32 microcontroller families, selected microcontrollers of the introduced Renesas Rx family and Synergy S1/S3 family also offer an above-average degree of coverage with regard to security features. Microcontrollers in the Synergy S5/S7 category (Renesas) even meet this requirement fully (Figure 4). In addition, fully integrated support for both symmetrical and asymmetrical encryption methods, including integrated key generation based on AES (128/192/256), 3DES/ARC4 or RSA/DAS or DLP, should be emphasized here. The Rx family can be seen as a pioneer in terms of full coverage of various security features as well as support for integrated mechanisms in symmetrical and asymmetrical encryption. Infineon’s XMC-1xxx and XMC-4xxx series also offer extensive integrated security data protection – for further details see the security aspects white paper [1] pp. 74–75. Within the context of special requirements for symmetrical or asymmetrical encryption, the supplier refers to the crypto software package. Based on their own assessment of security risks for the end-product and its component parts, developers can see at a glance which microcontrollers can potentially be used to ensure compliance with the general data protection regulation (GDPR) in board design.
If a developer defines security requirements for the end-product, the Rutronik product portfolio offers a wide variety of microcontroller families from semiconductor suppliers that meet the challenges of GDPR legislation by integrating security-relevant features.
Summarizing, the key finding in relation to industry 4.0 remains that data and services are not a product but a platform business. In future the matter will focus less on selling machinery to generate high revenues. Instead a wide variety of different data generating machines will be installed on site, and the platform operator will primarily earn money from the customer through related data services. This will mark a revolutionary change to business models in the traditional plant and machinery manufacturing industry and its component suppliers.
Literature
[1] Security aspects, Rutronik, white paper: How to Make State-of-the-Art Electronic Designs. Available under http://www.rutronik.com/security-aspects
The Author

Martin Motz,
graduated from the Leningrad Electrotechnical Institute (LETI) with a degree in microelectronic components technology. His career started in the development and prototype production of optoelectronic semiconductors and thinfilm hybrid circuits.
After working in materials research, he was a product manager in different companies and worked for 20 years in strategic marketing of automotive ICs for an international semiconductor company, before joining Rutronik in 2011 as product marketing manager for microcontrollers.
Martin.Motz@rutronik.com
- Security first
- Preventing manipulation





