Protection against hacking
Security first
In combination with software, microcontrollers form the heart and soul of sensor technology within industry 4.0 and IoT technologies. While connectivity of smart factories and smart homes offers immense potential for growth and innovation, it also makes them vulnerable to attack.
Microcontrollers are increasingly becoming the shield against manipulation and cyber attacks in the context of the IoT, industry 4.0, and robotics. Some microcontroller families already incorporate an array of security features (Figure 1). Microcontrollers are the key control components in connected systems. Suppliers are already employing development processes certified in line with the relevant security standards. Through their secured manufacturing chains, semiconductor suppliers also ensure that they can offer their customers a secure end-to-end solution.
Microcontrollers can be categorized in terms of security according to their target applications: authentication solutions and trusted platform modules (TPMs), such as for brand protection and IoT networks, banking and identification solutions for classic smartcard companies in payment processing, personal ID, transport and pay TV sectors, mobile security for SIM-based solutions in mobile products and machine-to-machine (M2M) applications, automotive solutions for near-field communication (NFC, eSE) and secure driving.
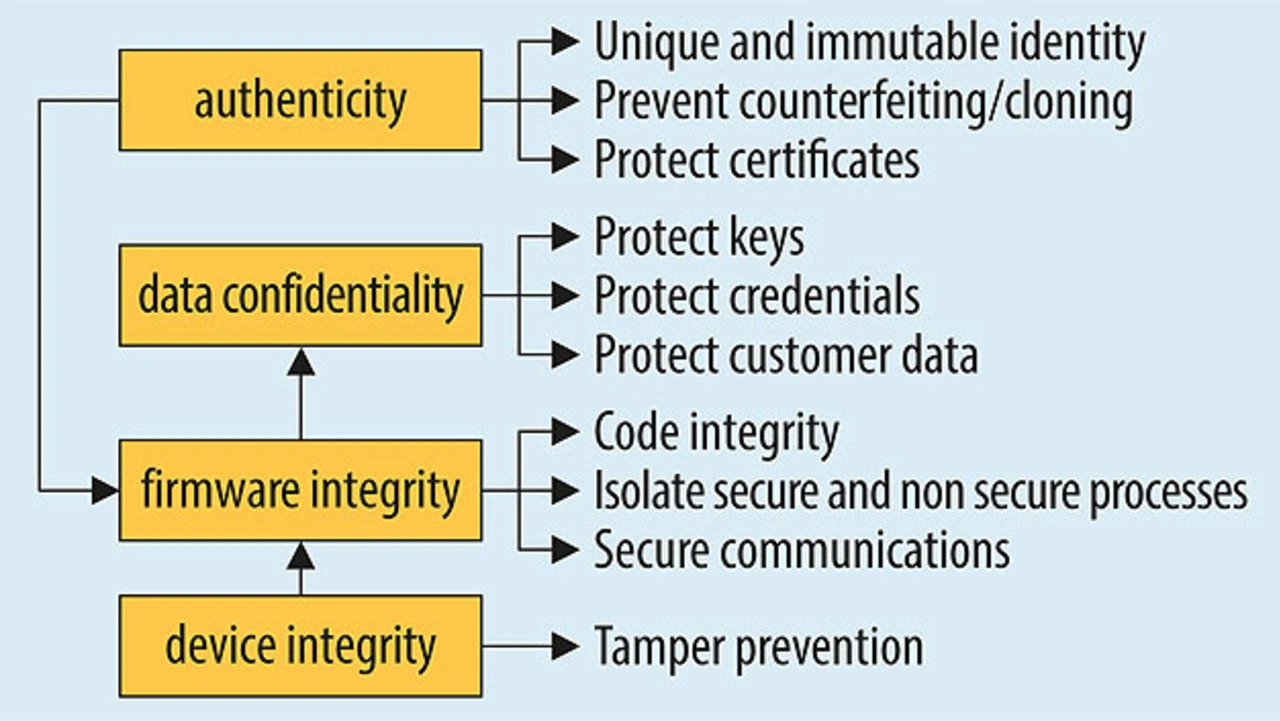
Integrated data security features
The IoT, industry 4.0, and robotics mostly use standard microcontrollers for industrial and consumer applications (general-purpose microcontrollers). Models with integrated security features are also already available. The STM32 family, for example, has many features offering protection against: identity theft (protection against manipulation, integrity protection, traceability), denial of data service (throttling), data and code spying and manipulation (memory protection, rights management, debug level, secure firmware updates), physical/mechanical attack (on-chip manipulation protection). These features are primarily implemented by on-chip integration (Figure 2).
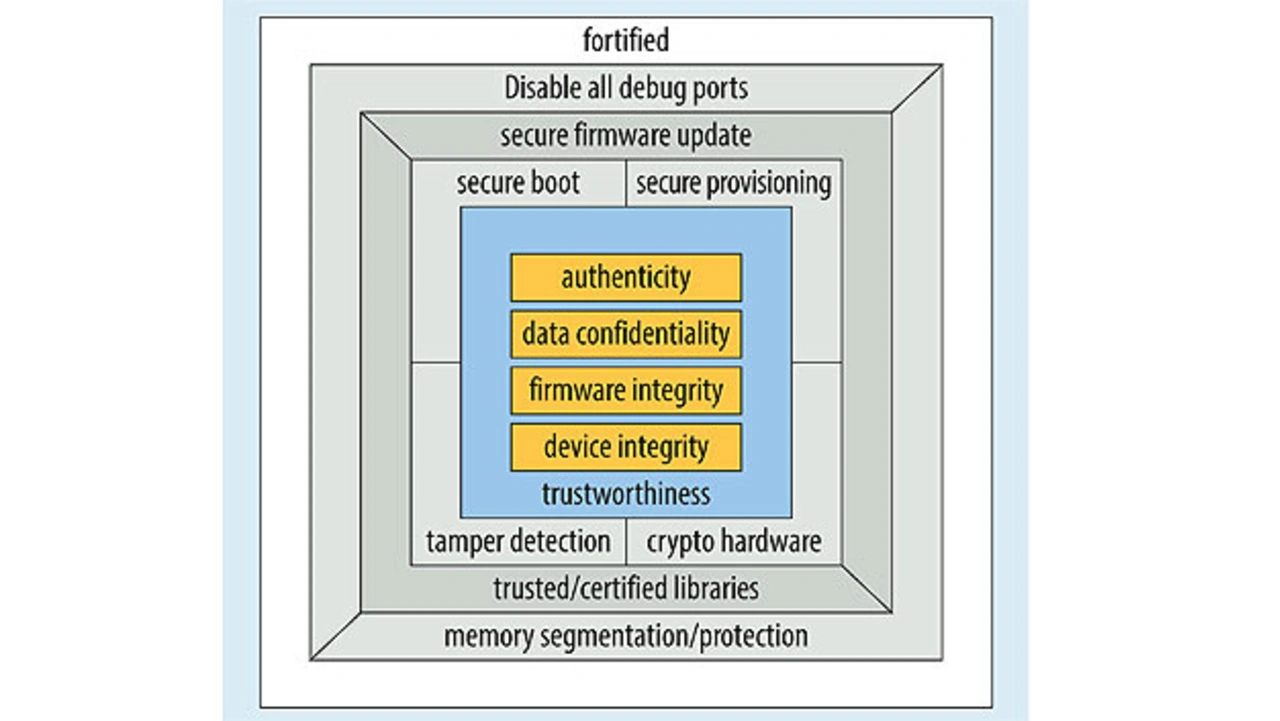
They ensure robust authentication, platform integrity, and thorough data security, including the resultant protection of end users’ privacy as well as comprehensive data, IP and branding protection – and as such meet the highest data security demands for standard products. Typical target applications include printers, computers, gateways, IoT end-points, and sensors.
Hardware-based functions
Integrity and operational security: the cyclic redundancy check calculates a checksum that identifies errors in data transfer or storage. This not only provides an integrity check but also means a signature of the software can be calculated during its runtime. Power monitoring is a high-security method: POR flag status (power on reset), PDR flag status (power down reset), BOR flag status (brown-out reset) and PVD flag status (programmable voltage detector) are capable of determining the reason for a reset and thus ensuring that reset is carried out by authenticated access. This is complemented by the read-while-write function for efficient detection of manipulation and logging.
Functionality of the clock security system (CSS) is based on the fact that both the clock and the system to restore it, as well as internal and external clocks, work independently of each other. The watchdog and the window watchdog likewise monitor time windows independently of each other. Integrity and trustworthiness of memory contents are ensured by the error correction code (ECC) and parity check. They also provide added protection against attack aimed at infecting systems with bugs. A temperature sensor continuously measures ambient temperature of the IC to ensure it remains within the specified range, thus avoiding the risk of lasting damage by targeted heating.
Encryption – the right way
Encryption techniques protect a source text against unauthorized access by encoding the original plain text. Anyone who cracks the code can thus also decipher the encrypted text. More advanced encryption techniques are symmetrical or asymmetrical. The symmetrical method means there is only one key for both encryption and decryption, so the sender and recipient use the same key. By the asymmetrical method each of the communicating parties uses their own key, with which a key pair is created. This consists of a public key with which data are encrypted, and a private key to decrypt it.
In some STM32 series a genuine random number generator is fully integrated into the chip for encryption purposes (Figure 3). This is based on the symmetrical advanced encryption standard (AES). The STM32 F2, F4, F7, L4 series feature keys optionally of 128/256 bits in length, employing various methods (ECB, CBC, CTR, GCM, GMAC, CMAC), while 128-bit AES is implemented in the STM32 L0/L1 series.
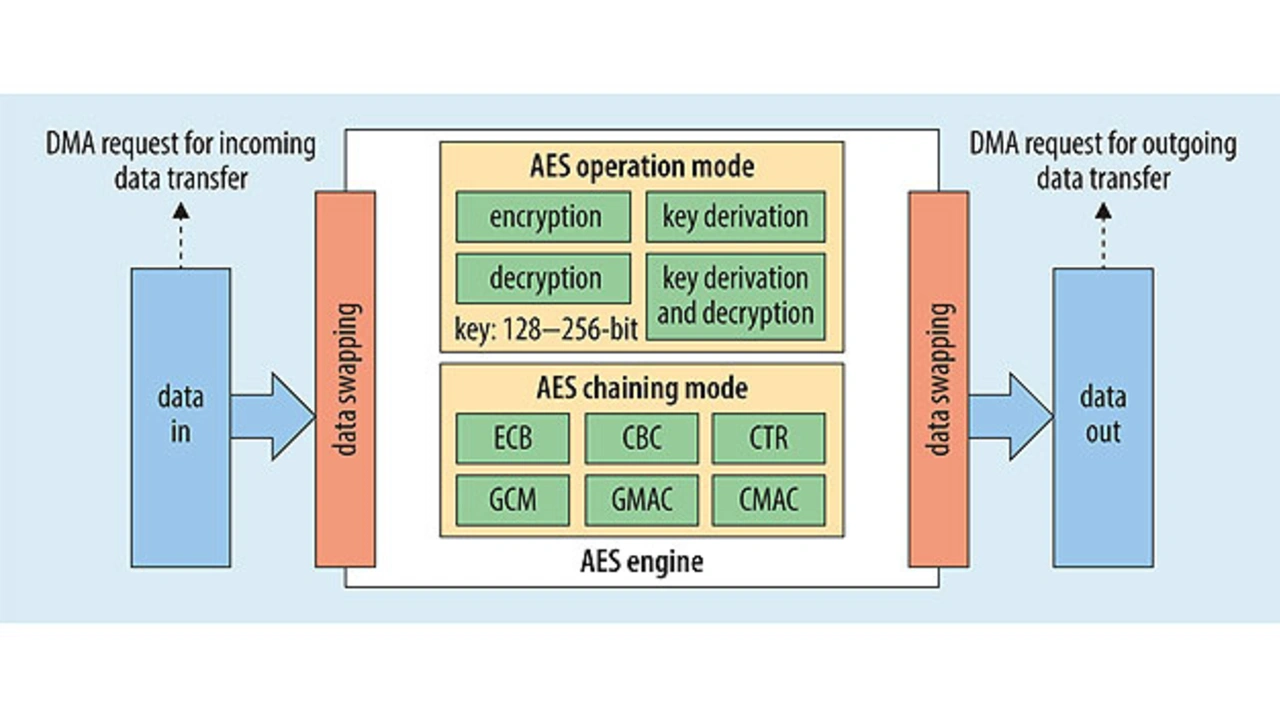
The advantage of the symmetrical method – as there is only one key, management is simpler than by the asymmetrical method. Encryption and decryption are also executed much faster. Some STM32 models additionally feature a fully integrated hash function. Here data are chopped up and scattered, and the function maps a large input volume to a smaller target volume. There is also the keyed hash message authentication code (HMAC), where structuring of the message authenti¬cation code (MAC) is based on a cryptographic hash function. HMACs are specified in RFC (request for comments) 2104 and in NIST (National Institute of Stan¬dards and Technology) standard FIPS 198.
- Security first
- Preventing manipulation





