Comprehensive Security Framework of ASA
Securing Future High-Speed Video and Sensor Data Architectures
With level 3 autonomous driving starting to be rolled out, securing the communication inside cars is not a nice to have, but ever more important. This includes the need to protect high-speed video and sensor data used in respective driver assist systems.
Security covers a large field of methods and algorithms, from which a wise selection must be made. This article explains the importance of link-based security for protecting high-speed video and sensor data, which is supported with Automotive Ethernet and ASA Motion Link SerDes communication. Furthermore, the article discusses how an intelligent key exchange mechanism, like defined for the ASA Motion Link, ensures protection as well as a lean implementation for the sensor modules, while facilitating interoperability between ICs of different semiconductor suppliers.
It is a no brainer that every even only partially autonomously driving car needs to undergo a severe risk assessment concerning security. The driver’s and passengers’ safety are of utmost concern to car manufacturers and legislation alike. Any risk of a malicious attack affecting the driving function or the drivers’ decision making must be reduced to an absolute minimum. Cyber security mechanisms have thus become an essential element of every vehicle Electric and Electronics (EE)-architecture, an element that is ever more important with the growing amount of data exchanged inside cars.
Especially in the case of cameras and sensors, cyber security serves a broader purpose though. Cameras and other driver assist sensors are often connected to the outer shell of the car and may need to be replaced after accidents. Cyber security helps to prevent that this is done with stolen or counterfeit parts, thus protecting other car owners from finding their sensors stolen and ensuring that the replacement parts comply with the car manufacturers quality requirements. This ensures to preserve the safety level that the car manufacturers are responsible for. Finally, cyber security can also protect the car users’ privacy and complete vehicles from being stolen.
Security needs to accommodate different video architectures
The key goal of cyber security is to ensure Confidentiality, Integrity, and Availability (CIA).This is typically achieved by a combination of authentication and/or encryption algorithms with key exchange mechanisms. The optimum realization thereby also depends on the type of communication architectures that needs to be protected. Figure 1 provides an overview of typical architectures for sensor and displays, in which the sensors and displays have no software processing capabilities themselves. They communicate raw, high-speed (video) data. For simplification reasons the sensors and displays in Figure 1 are connected to the same processor and processing unit. Note, that this is not necessarily so. Sensor data might be processed in units different from the one that renders the video image for the displays. In the context of this articles, it makes no difference though whether the same or separate processing units are used.
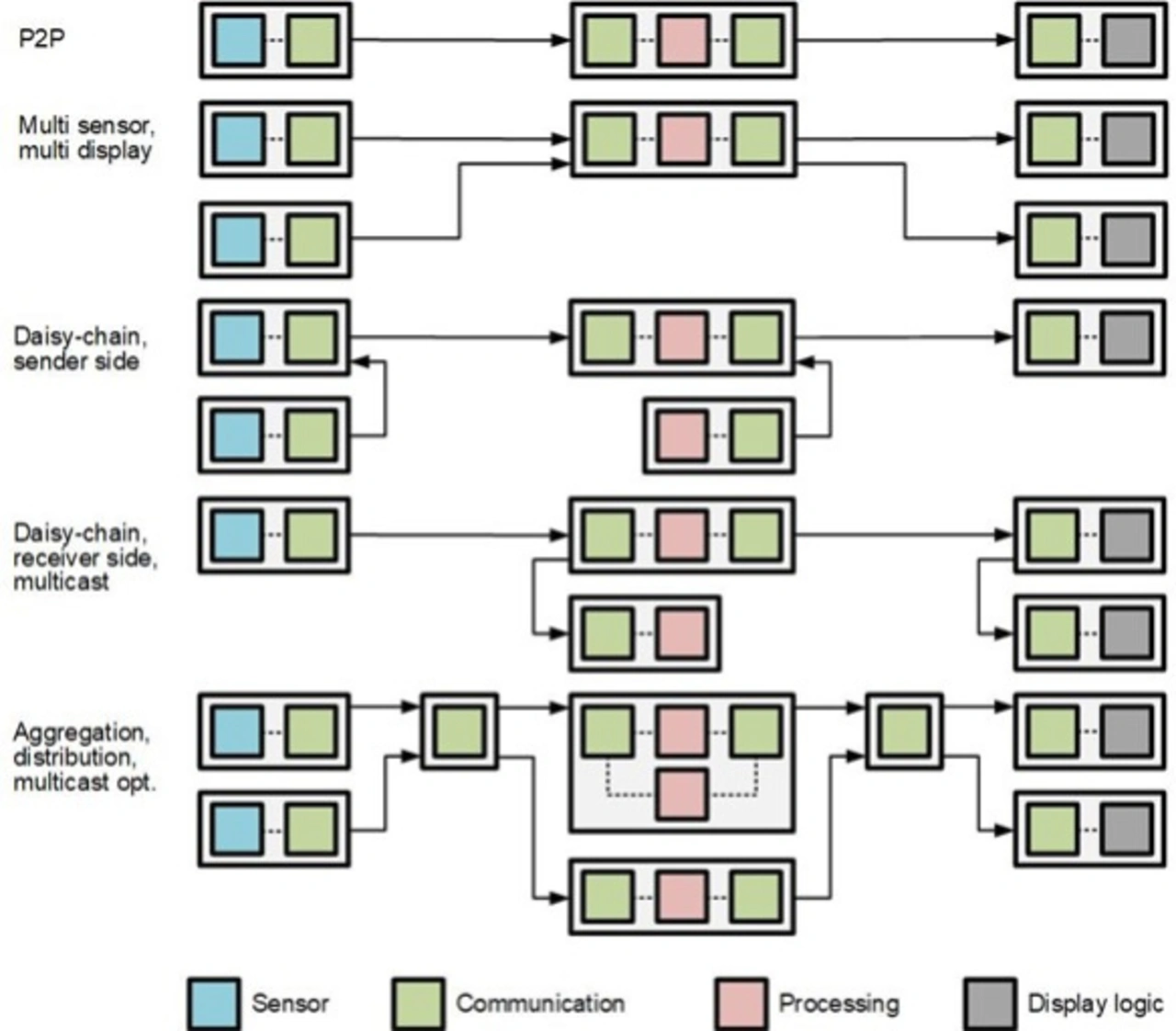
The scenario often associated with (camera) sensor and display links is Point-to-Point (P2P) connectivity, which is depicted in the top row of Figure 1. In case of P2P, a single sensor or display is connected to a single (video) data processing unit by a direct, dedicated link in a one-to-one relationship. Note that while this scenario seems typical, it is actually not that likely, especially in any forward-looking architecture. Figure 1 therefore shows other architecture options. These include multiple sensors, displays or processors, which share communication as well as processing power, which are daisy-chained, whose video streams are aggregated or distributed among different units or distributed within one unit to/from different processors, or whose data streams are multi-casted. Real architectures are likely to be a mix of all depicted options. The selected security concept thus needs to support all.
Link-based security provides the foundation
Security mechanisms can be applied to different layers of the communication protocol stack. For the sake of this article, we distinguish between link-based, protocol-based, and application-based security only. Link-based security protects the physical layer of the communication technology and starts and ends in the communication chip (see Figure 2). Examples are MACsec for Ethernet or the ASAsec for the ASA Motion Link. Protocol-based security is a mechanism applied to a higher layer protocol that would typically start and end in the chips that generates, processes, or displays the sensor/video data (see also Figure 2). Examples are IPsec, Transport Layer Security (TLS) for Ethernet or the security defined with the MIPI Camera/Display Service Extension (CSE/DSE). Finally, any sensor or video processing chip can add authentication or encryption on application level, which would also end in the sensor, display, and processing chips and which is typically vendor specific. This means that should the two end chips be from two different vendors, they have to have the respective knowledge and capabilities concerning the security supported by the respective other chip.
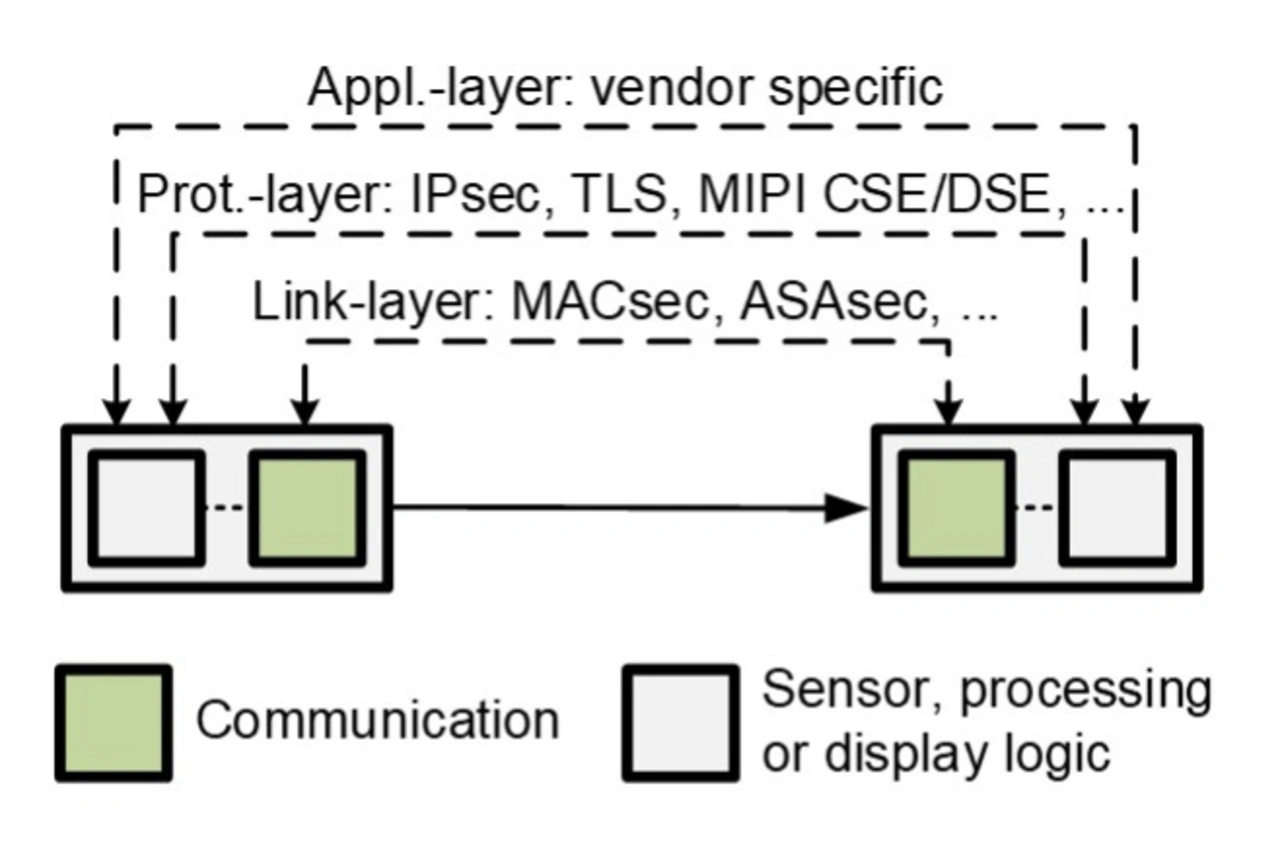
While there are differences between protocol-based and application-based security, we can, for the sake of this article, reduce the distinction between link-based and end-chip to end-chip-based security (Ec2Ec); the term “End-to-End (E2E)” that is often used in the context of functional safety, cannot really be applied to security. While Ec2Ec seems desirable, Figure 3 provides an idea how the complexity this causes in EE-architectures beyond P2P on every hop, becomes prohibitive, as the number of E2E relationships explodes. The example scenario depicted in Figure 3 could be a simple surround-view scenario, in which the data streams of four cameras are connected to one unit in which two processors access the data (e.g., one for autonomous driving functions, the other for a parking aid system). In case of link-based security (see left side of Figure 3), there would be four security relationships. In case of an Ec2Ec protected scenario there would be eight security relationships, that additionally must handle multi-cast streams, with now two ends to one source. In contrast, for the protection algorithms of link-based security in the discussed high-speed sensor and video connectivity scenarios, it makes no difference whether unicast or multicast data is being transmitted or how many different data streams are transmitted across the same link.
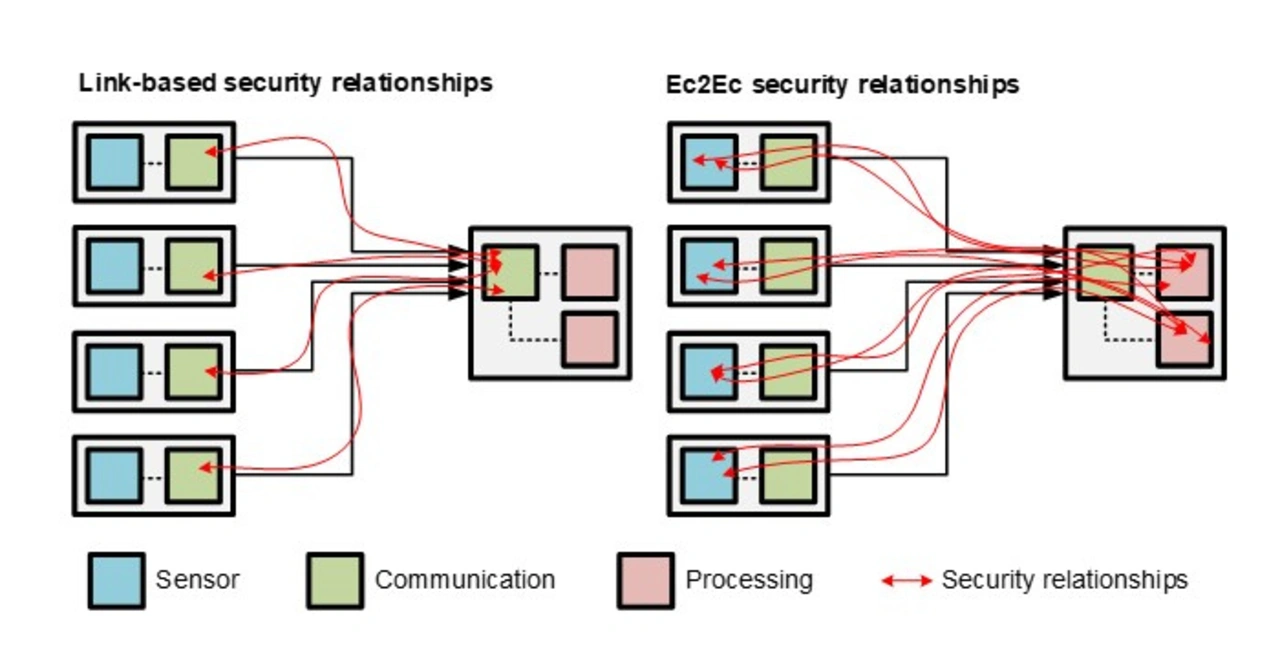
Link-based security decouples the security from the application. It thus significantly reduces complexity and undesirable interdependencies between sensor, display, and processing chips (and their vendors). This is the reason why many car manufacturers have already selected MACsec as the security mechanism for their in-vehicle Ethernet networks. There is no reason, why this should be any different for high-speed sensor and display use cases. Should it really be necessary to additionally protect specific data Ec2Ec, link-layer security always allows to add additional security layers. In contrast, if link-layer security is not supported by the communication technology selected, it cannot be added later.
An efficient key exchange mechanism is key to efficient sensor implementations
The automotive industry discusses high-speed video and sensor data architectures in cars not only because car manufacturers would like to perform their centralized processing on raw data, but also because car manufacturers like to avoid software and software updates in peripheral units, whenever possible. When adding security to cameras or other sensors, it is therefore important that the encryption and authentication algorithms as well as the key exchange mechanisms of the selected technologies allow hardware accelerated/firmware only implementations plus enough efficiency to increase the processing power only minimally (display links do not face the same criticality). One of the key distinctions is thereby made between algorithms using symmetric or asymmetric keys.
The security defined for the ASA Motion Link provides for authentication, integrity protection, and (optional) encryption using a three-level symmetric key exchange mechanism, with device keys, binding keys, and link keys. By defining one solution optimized for the use case, the complexity of ASAsec has been minimized. This is a learning from implementing MACsec in automotive networks, as MACsec unnecessarily (from the automotive perspective) allows for several implementation options such as supporting asymmetric keys with the Extensible Authentication Protocol (EAP).
The advantage of symmetric keys is that the usable crypto algorithms, such as Advanced Encryption Standard (AES), are faster, more efficient, and readily available with hardware acceleration. This is different for the alternatives available for asymmetric keys such as Elliptic Curve Cryptography (ECC) or Rivest-Shamir-Adleman (RSA). The efficiencies of both are hampered by many variants and curves, as well as certificates. With key sizes of 4096 bits and larger, ECC and RSA are difficult to implement in hardware, but require software support, which is undesirable in small sensors. The key handling is somewhat more complex for symmetric key security than for asymmetric key security. However, this complexity affects more the key management at the car manufacturers – who typically already support this for other use cases – than the actual implementation inside the sensors. The ASAsec design thus allows a very smart design by moving a little of the complexity to the car manufacturers internal processes.
The ASA Motion Link technology has been developed to efficiently support asymmetric high-speed data communication as needed especially for connecting camera and display modules without software processing capabilities inside the EE-architecture. Allowing for a uniform architecture is gaining importance just now, with more sensor types – e.g., radars, lidars – being discussed for being realized and connected in a similar fashion (no software processing in sensor but higher data rates to transmit). Cyber security is thereby a relatively new requirement for the communication. In case of ASA Motion Link, the technology was designed with security right from the start and without having to take any compromises, which often happens when security must be added later.
The advantages are the enabling of an application independent link-based security mechanism and a defined, efficient key exchange mechanism with symmetric keys. This is the only way to reduce complexity and overhead in the processing units, while allowing safe and secure sensor implementations from multiple vendors.







