RISC-V enclaves
A clean slate approach to Linux security
Two renowned security experts propose a new zero trust computing model based on the concept of multi zone Linux enclaves for the free and open RISC-V ISA.
We live in the era of the Internet-of-Things (IoT). Billions of interconnected embedded devices are now an integral part of our lives. As these systems are connected to the Internet, they are inherently exposed to an endless number of cybersecurity threats. As shown by many recent high-profile cybersecurity incidents, the viability of this new Internet era heavily depends on the security of these devices and the trust we are willing to put on them.
Embedded Linux systems are intrinsically not secure
The root cause of the never-ending cat-and-mouse game of exploits and patches is due to the intrinsic lack of separation built into the prevailing computing model. Mainstream operating systems like Linux are built according to a monolithic architecture where kernel modules have indiscriminate privileged access to any resource of the system.
A typical example is the Linux implementation of the TCP/IP stack, which is an integral part of the kernel and, by definition, exposed to remote attack – the most damaging category of cyber threats. This makes the kernel the single point of failure and the main avenue for attacks via privilege escalation. In addition, recent research has demonstrated how the microarchitectural components of modern high-performance processors – e.g., caches, branch prediction, out-of-order execution – can be exploited to conduct timing side-channel attacks and to interfere with determinism, predictability, and in the end, with the reliability of the whole system.
RISC-V, the free and open ISA, has the potential to become a security game-changer by defining a comprehensive set of security building blocks in the ISA itself, which are then present in every silicon implementation. Some of these features include:
- four privileged execution levels,
- physical memory protection (PMP), and
- user-mode interrupts.
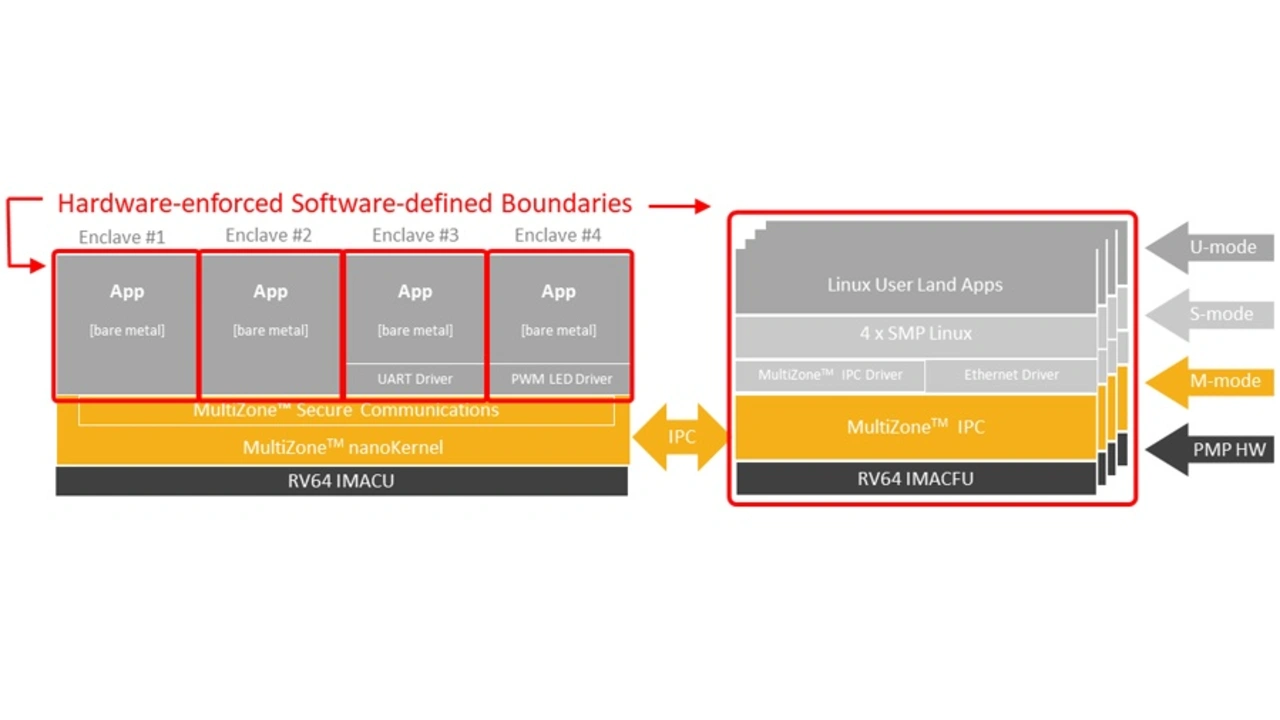
Multi zone Linux enclaves
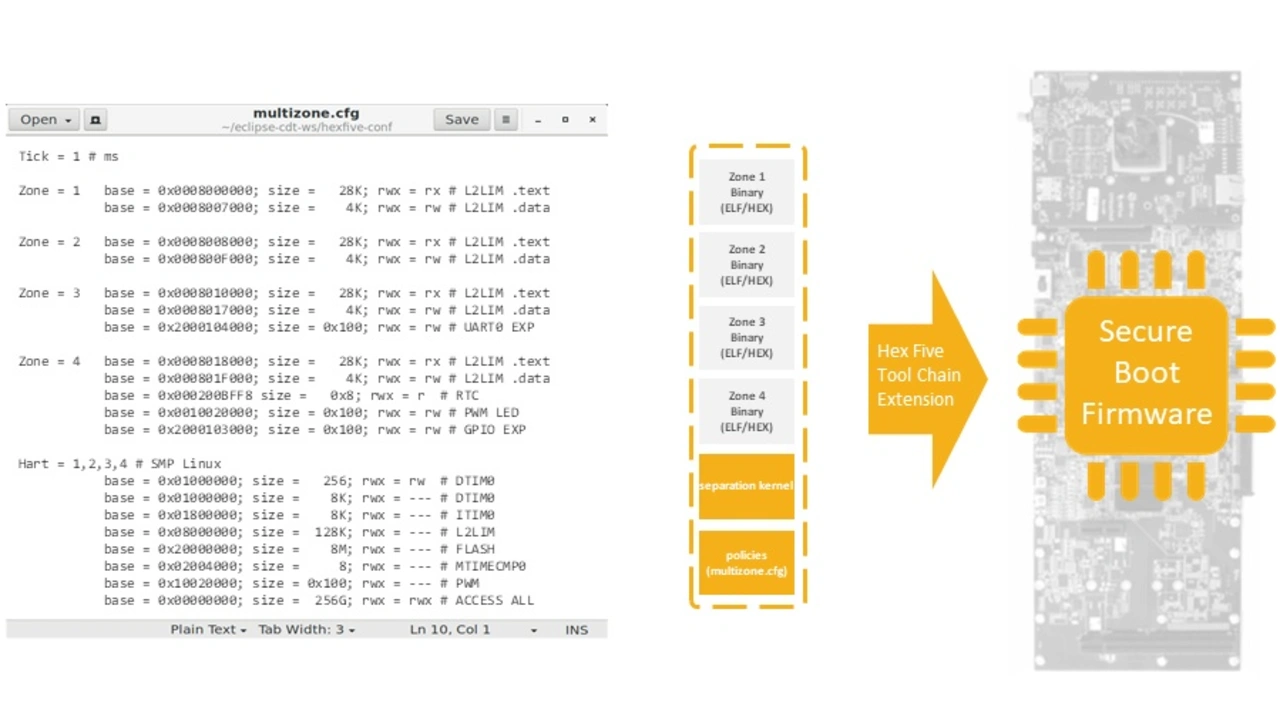
As the functional requirements have become more complex, embedded system designers have no other choice but to rely on readily available 3rd party software. In some case the source code is available for analysis and security validation – i.e. open source software, in some case it is available as opaque linkable object modules, in some other cases the source code is proprietary and completely hidden from scrutiny – i.e. binaries.
The requirement has emerged to enforce the separation, or firewalling, of the various software components within the system. However, complexity, code base size, and attack surface of a rich operating system that can provide virtual memory separation are simply unfit for the level of trust required in safety-critical applications.
To address these requirements, a resilient multi zone enclave for embedded Linux applications must provide:
- An extremely limited attack surface, in the order of few kilobytes, equivalent to a TCB of less than 1,000 lines of code. Formal verification and a conservative 1 defect per 1,000 lines of code ratio guarantee the absence of vulnerabilities.
- Completely self-contained with zero dependencies from libraries and other runtime components including C runtime, linker scripts, and kernel-mode drivers.
- Isolation of executable code (text segments) to ensure that user programs run in unprivileged mode so that they can’t compromise the overall system integrity.
- Isolation of data (data segments) and memory-mapped peripherals (I/O) via a hardware unit that prevents access outside statically defined security boundaries.
- Isolation of hardware interrupts so that interrupt handlers are mapped to the respective enclave context and executed at a reduced level of privilege, unable to compromise the isolation model.
- Isolation of cores and other microarchitectural resources (e.g., caches) in heterogeneous systems such that low-criticality/non-secure core(s) cannot compromise and/or interfere with high-criticality/secure core(s).
The authors

Dr. Ing. Cesare Garlati
is a renowned expert in information security. Former Vice President of mobile security at Trend Micro, Cesare is the founder of Hex Five Security and the inventor of MultiZone, the first Trusted Execution Environment for RISC-V processors.
Cesare is a long-time supporter of open source software and open standard technology, former Chief Security Strategist at prpl Foundation, and an active member of the RISC-V Foundation. He has delivered presentations and highlighted speeches at many tier-1 events, including embedded world Conference, IoT World, Mobile World Congress, Gartner Security Summits, IDC CIO Forums, CTIA Applications, CSA Congress, DAC, IoT Innovation and many editions of the RSA Conference – the world’s leading information security event.
Cesare holds an MBA from U.C. Berkeley, a Master in Electrical Engineering and Computer Sciences, professional certifications from Microsoft, Cisco and Oracle, and he is a Fellow of the Cloud Security Alliance, where he founded and chaired the Mobile Security and the IoT Security groups.

Prof. Dr. Sandro Pinto
is a Research Scientist and Invited Professor at the University of Minho, Portugal. He holds a Ph.D. in Electronics and Computer Engineering. During his Ph.D., Sandro was a visiting researcher at the Asian Institute of Technology (Thailand), University of Wurzburg (Germany), and Jilin University (China).
Sandro has a deep academic background and several years of industry collaboration focusing on operating systems, virtualization, and security for embedded, cyber-physical, and IoT-based systems. He has published several scientific papers in top-tier conferences/journals and is a skilled presenter with speaking experience in several academic and industrial conferences.
Sandro is a long-term supporter of open source projects, a proud member of the RISC-V Foundation, and is currently helping Hex-Five make embedded security practical at scale.








